0x1 刷rom
kali:http://docs.kali.org/kali-on-arm/install-kali-linux-arm-raspberry-pi
img:https://www.offensive-security.com/kali-linux-vmware-arm-image-download/
通过dd直接刷入sdcard:
1、解压img包
img:https://www.offensive-security.com/kali-linux-vmware-arm-image-download/
通过dd直接刷入sdcard:
1、解压img包
xz -d *.xz
2、获取sdcard盘符
diskutil list
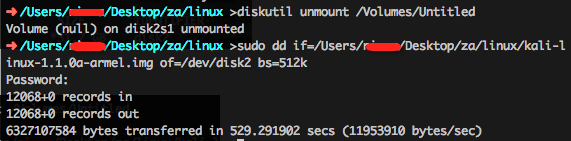
3、卸载U盘挂载
diskutil unmount /Volumes/Untitled
4、刷入系统
sudo dd if=kali-1.0.9-rpi.img of=/dev/sdb bs=512k
0x2 通信方式
0x21 SSH
ssh [email protected]
亦可nmap扫描内网ssh端口来确认ip:
0x22 VNC
需知ip,并安装启动vnc服务
apt-get install vnc-server
vncserver
vim /root/.vnc/xstartup
xrdb $HOME/.Xresources
xsetroot -solid grey
x-terminal-emulator -geometry 80x24+10+10 -ls -title "$VNCDESKTOP Desktop" &
x-window-manager &
#Fix to make GNOME work
export XKL_XMODMAP_DISABLE=1
/etc/X11/Xsession
vncserver
vnc_client:xxx.xxx.xxx.xxx:1
(自定义分辨率 :vncserver -geometry 1024x768)
0x23 USB to TTL
0x231 串口图示
GND->Groud
RXD->GPIO 14(TXD)
TXD->GPIO 15(RXD)
0x232 连接
1、装ttl芯片驱动
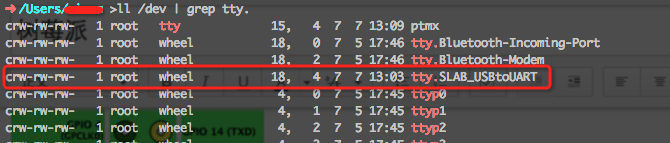
2、查看tty设备
2、查看tty设备
ll /dev | grep tty
3、screen连接设备
screen /dev/tty.SLAB_USBtoUART 115200
0x3 绵羊墙
网卡:TP-LINK TL-WN722N
0x31 kali+AP Rouge+mitmproxy
脚本:kali + AP Rouge + mitmproxy
0x32 kali+mana
绵羊墙大致方案是:树莓派+kali+mana
mana可以参考以下:
https://cyberarms.wordpress.com/2014/10/16/mana-tutorial-the-intelligent-rogue-wi-fi-router/
https://www.pwnieexpress.com/bypassing-hsts-ssl-with-the-mana-toolkit/
https://forums.hak5.org/index.php?/topic/33783-raspberry-pi-b-mana-tool-kit-hack-google/
http://drops.wooyun.org/tips/4634
http://api.weixin.soften.cn/view.php?id=5452f4b07f8b9a91658b458c&count=&hl=
http://j4s0nh4ck.iteye.com/blog/2170489
mana可以参考以下:
https://cyberarms.wordpress.com/2014/10/16/mana-tutorial-the-intelligent-rogue-wi-fi-router/
https://www.pwnieexpress.com/bypassing-hsts-ssl-with-the-mana-toolkit/
https://forums.hak5.org/index.php?/topic/33783-raspberry-pi-b-mana-tool-kit-hack-google/
http://drops.wooyun.org/tips/4634
http://api.weixin.soften.cn/view.php?id=5452f4b07f8b9a91658b458c&count=&hl=
http://j4s0nh4ck.iteye.com/blog/2170489
0x321 git
git clone --depth 1 https://github.com/sensepost/mana
cd mana
git submodule init
git submodule update
make
make install
0x322 kali apt-get
apt-get install mana-toolkit
启动脚本:
log:
/usr/share/mana-toolkit/run-mana/start*.sh(建议使用start-nat-full.sh)firelamb-view.sh来查看捕获的sessionlog:
/var/lib/mana-toolkit
注意:mana默认dns为8:8:8:8,国内环境不一定能连上





没有评论:
发表评论